Keyed locks are relatively easy to pick if you’ve spent enough time mastering the skill. But researchers at the National University of Singapore have just made it even easier. If you can use a smartphone to record a sound, you can capture all the information you need to create a working duplicate of a key.
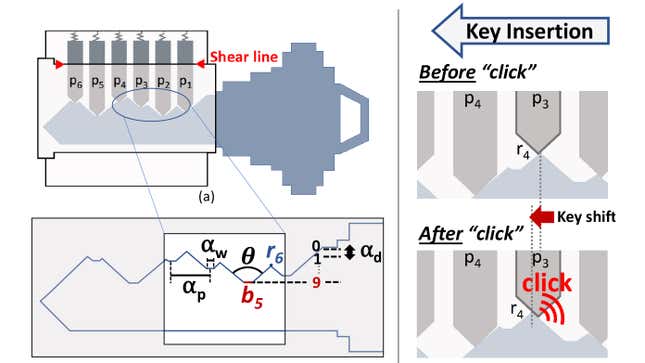
The newfound vulnerability—although it’s more a case of modern technology compromising an outdated technology—was discovered by cyberphysical systems researcher Soundarya Ramesh and a team at the National University of Singapore. The attack, called SpiKey, works on what are known as pin tumbler locks that are opened using a key with a unique ridge pattern on its edge. As the key slides into the lock, the ridges push six metal spring-backed pins to different heights which, when all are properly aligned, allow a tumbler to turn and a lock to be opened. They’re one of the most common types of locks out there, used in everything from doors to padlocks, which makes this attack especially concerning.
To open a pin tumbler lock without the key, a locksmith (or lock pick) uses a specialized set of tools to manually adjust the height of each pin, one by one, until they figure out the unique arrangement needed for the tumbler to turn. The SpiKey technique is magnitudes easier, and requires little to no special skills, aside from the ins and outs of operating a 3D printer.

The research team found that the sounds the ridges on a key make as they collide with the spring-loaded pins while being inserted into a lock, and the time between each metallic click, can be analyzed and reverse-engineered to determine the shape of the key, or at least a close match. While a six pin lock has something close to 330,000 possible key shapes, the SpiKey attack can narrow that down to just three, which are relatively easy to quickly work through and test.
There are some challenges to the technique, however. The SpiKey software has some error correction built-in, but it mostly requires a key to be inserted into a lock at a constant speed for the recorded sounds to be successfully analyzed and reverse-engineered. If you’re worried about someone using the technique to get into your house, from here on out just use erratic jerky motions when inserting your key into the deadbolt. The attacker also has to be very close to the lock if using a smartphone to record the sounds to get enough audio fidelity for the software to properly do its thing—less than four inches away, which makes performing a covert attack using SpiKey very challenging. But the researchers suggest that malware installed on a target’s smartphone could be used to record the sounds of a lock they’re opening, or a smart doorbell, often mounted right next to a door, could potentially be compromised and used to record the needed sounds.
That’s assuming the surrounding area is relatively quiet, without traffic rushing by, or other sounds that could compromise the recording. It’s not a foolproof attack, at least not yet, so for the time being you can easily keep yourself safe by just singing Journey’s Don’t Stop Believin’ at the top of your lungs every time you get home and unlock the front door—assuming you don’t do that already.