Microsoft Confirms Details Of Security Breach
Yesterday, we learned that Microsoft may have been a target of the hacking group LAPSUS$, which published a compressed archive of what appeared to be Microsoft code. While Microsoft said at the time that it was investigating the groups' claims, now the company has confirmed it was indeed attacked by the group. Not only that, but Microsoft has detailed the extent of the attack.
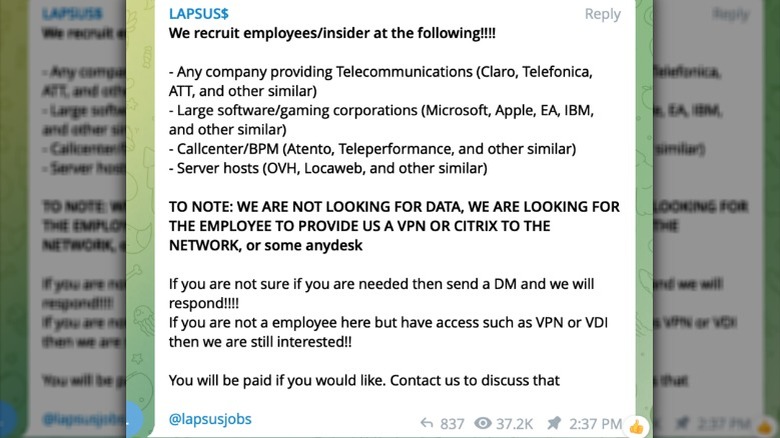
It's all detailed in a lengthy post to the Microsoft Security Blog. Microsoft opens by noting that its security teams have been "actively tracking a large-scale social engineering and extortion campaign against multiple organizations," in recent weeks, and that it has attributed that activity to LAPSUS$, otherwise identified as DEV-0537 in that blog post. Microsoft goes on to say that LAPSUS$ stands out somewhat from other hacking groups in that it announces its targets via social media and openly advertises attempts to buy internal access from employees of the companies it plans on attacking — something that was revealed as other security researchers dug into the group's history.
Microsoft details security breach and what the hackers took off with
Most of that security article is devoted to Microsoft's observation of LAPSUS$ and its methods, but there's also a section where the company details the actions the hacker group has taken against it. Microsoft says that LAPSUS$ gained access to its internal systems via a single compromised account. "Our cyber security response teams quickly engaged to remediate the compromised account and prevent further activity," Microsoft wrote, which goes along with LAPSUS$'s own claims that it lost access to Microsoft's servers in the middle of its attack.
All in all, it sounds like the impact this LAPSUS$ attack had on Microsoft is minimal, if there was any impact at all. Microsoft says that "no customer code or data was involved in the observed activities." Though the hackers did make off with source code for products like Cortana, Bing, and Bing Maps, Microsoft also said that it "does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk." In fact, Microsoft says that LAPSUS$ going public with this attack allowed its security team to intervene "mid-operation" and mitigate a "broader impact" before it happened.
Microsoft has tips for other companies, too
Microsoft ended its security article with some tips for other companies that may eventually be the target of one of these LAPSUS$ attacks. Microsoft recommends that other companies require multi-factor authentication and insulate themselves from SIM-swapping attacks, which means no two-factor solutions that rely on SMS.
That's a good security tip for everyone, whether they're an individual trying to keep their bank account secure or a global corporation that has customer data and proprietary information to keep safe. Microsoft also recommends that companies tap into VPN authentication options and improve their awareness of social engineering attacks, which are again good tips for average consumers just trying to keep their personal accounts secure.
This may not be the last we hear from LAPSUS$ seeing as the group seems to be carrying out a string of attacks. With Microsoft publishing all this new information, however, companies may be able to better protect themselves from these attacks in the future. We'll see what happens from here, so stay tuned.